Let's Talk Cybersecurity Vulnerabilities #2
Real-world examples I've encountered
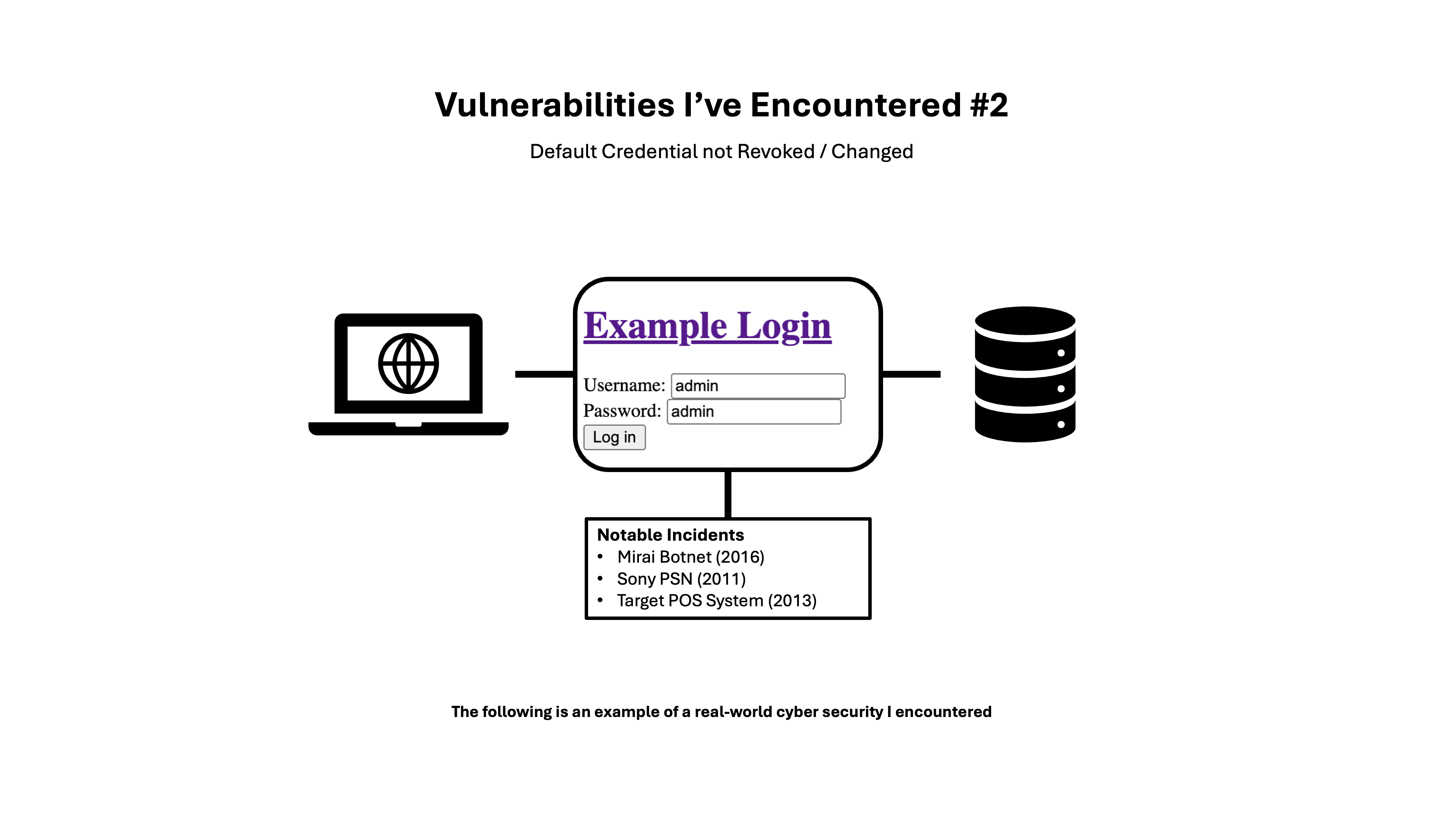
From random AirBnb WiFi Routers to Deployed Enterprise Systems, the textbook example of a high-risk but common vulnerability, unchanged default credentials:
Username:
admin
Password:
admin
These are often overlooked in rushed deployments, yet they're among the easiest ways for attackers to gain unauthorized access.
In this case, logging in with the defaults provided full backend access, including sensitive customer and operational data. No MFA, no IP restrictions, just a fully open door.
Default credentials are publicly documented and frequently targeted by automated tools. This issue has led to serious breaches, such as:
- Mirai Botnet (2016) - Infected over 600,000 IoT devices by scanning for default credentials
- Sony PSN Hack (2011) - Default credentials on network infrastructure played a role in the breach of 77 million accounts
- Target (Retail Shop) POS Breach (2013) - Default credentials on HVAC systems provided initial network access
Takeaways: Even the simplest misconfigurations can become massive vulnerabilities
- Revoke or change default credentials on all systems - Make this a mandatory step in your deployment process
- Regularly audit access controls - Create a schedule for checking credential policies and access rights
- Implement multi-factor authentication - Add additional layers to prevent credential-based attacks
- Use IP restrictions where possible - Limit administrative access to specific networks