Let's Talk Cybersecurity Vulnerabilities #1
Real-world examples I've encountered
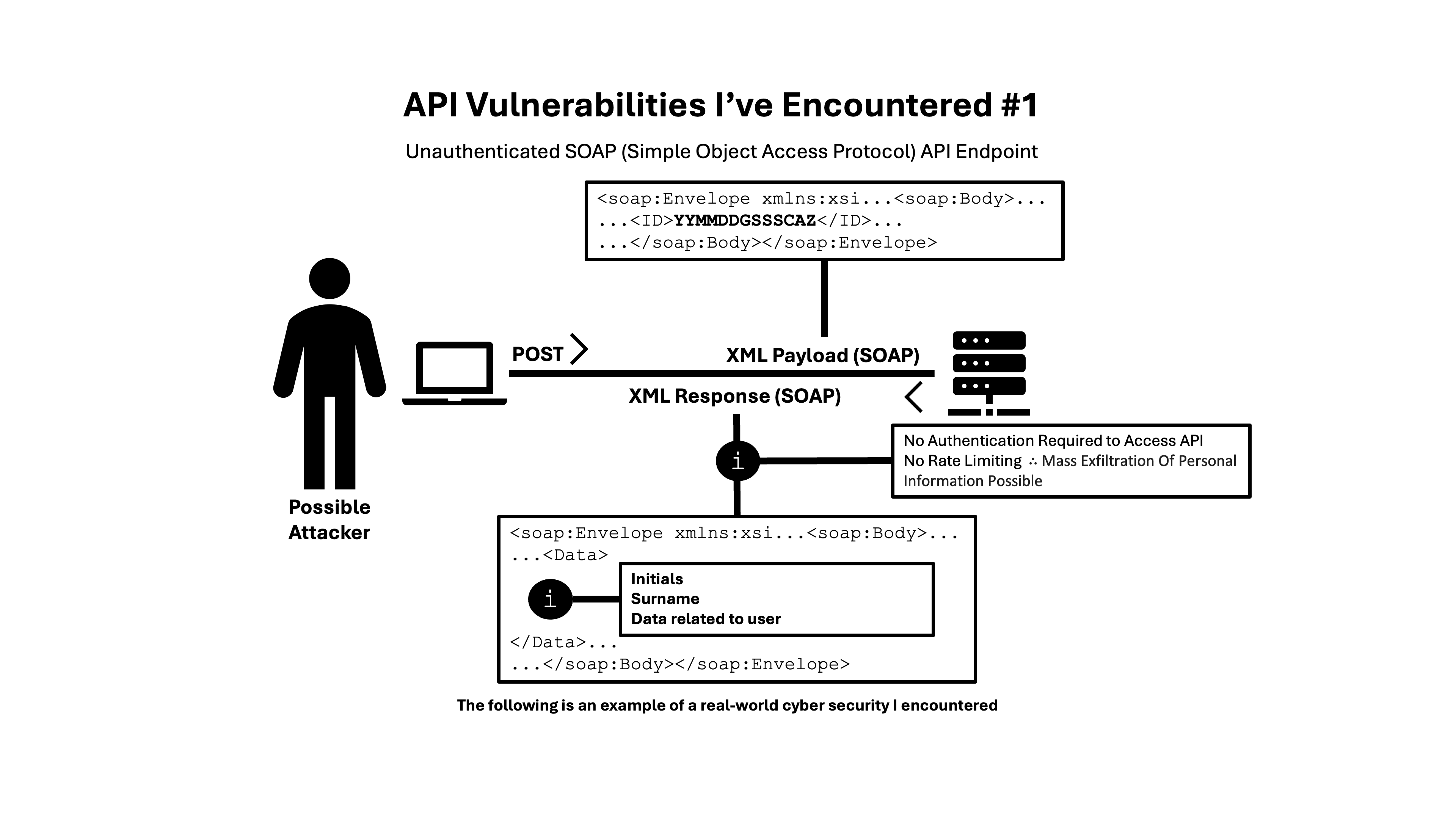
While exploring an old system, I found a serious issue, a SOAP API that required no authentication, had no rate limiting, and returned personal user data just by supplying an ID number.
SOAP (Simple Object Access Protocol) is an older XML-based protocol still used in many legacy systems. It's often forgotten when it comes to modern security practices.
In this case, a simple SOAP request returned initials, surname, and other personal info. Without protection in place, this allowed for mass data exfiltration with minimal effort.
<?xml version="1.0" encoding="utf-8"?>
<soap:Envelope xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
<soap:Body>
<GetUserInfo xmlns="http://example.org/api">
<userId>123456</userId>
</GetUserInfo>
</soap:Body>
</soap:Envelope>
<soap:Envelope xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
<soap:Body>
<GetUserInfo xmlns="http://example.org/api">
<userId>123456</userId>
</GetUserInfo>
</soap:Body>
</soap:Envelope>
Takeaway: Legacy systems can't be left behind when it comes to security.
- Always require authentication - No API should be accessible without proper authentication mechanisms.
- Implement rate limiting - Not just to slow down attackers, but also as a signal to detect unusual activity and flag potential breaches early.
- Audit old APIs before someone else does - Legacy systems often contain forgotten vulnerabilities that may be easy to exploit.
This example is unfortunately common, but completely preventable with proper security practices and regular system audits.